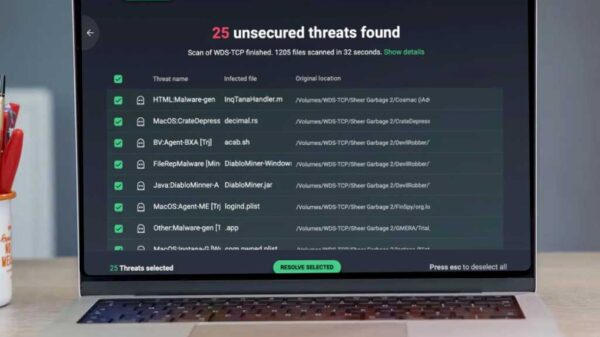
A recent cybersecurity breach known as the Salt Typhoon has revealed significant vulnerabilities in telecommunications and government networks. Attackers exploited outdated security flaws in widely used internet infrastructure, some of which date back to 2018. This incident highlights the importance of regular maintenance and updating security protocols, as the attackers remained undetected in these networks for a period ranging from nine to eighteen months.
According to Joshua Copeland, a cybersecurity expert at Tulane University, the breach was not the result of advanced techniques but rather a failure in basic upkeep and vigilance. No sophisticated tools were necessary for the attackers to gain access to sensitive systems. Instead, they took advantage of existing weaknesses that had not been patched, allowing them to infiltrate critical infrastructure.
The implications of this breach extend beyond the immediate security risks. Users may find themselves vulnerable without even realizing it. While individuals can easily cancel compromised credit cards, they cannot change their call logs or location histories, which can be exploited during future crises. Most consumers will not receive direct notifications about these breaches, as alerts typically go to service providers instead.
Urgent Need for Improved Cybersecurity Measures
The Salt Typhoon incident underscores a pressing need for comprehensive policy reform in cybersecurity practices. Experts argue that it is essential for leaders to adopt a proactive approach to patching vulnerabilities. This includes establishing firm deadlines for repairs and conducting regular audits to ensure compliance. Additionally, holding telecom companies to stringent standards for critical infrastructure can help mitigate risks in the future.
Copeland advocates for a shift from reactive incident response to continuous threat hunting. This proactive stance would allow organizations to identify and address vulnerabilities before they can be exploited. “We need to rethink how we approach cybersecurity,” Copeland stated. “Waiting for an incident to occur is no longer acceptable.”
Congress and regulatory bodies have a crucial role to play in this transformation. By prioritizing cybersecurity legislation and ensuring that telecom providers adhere to updated standards, they can help protect both networks and users. As the digital landscape continues to evolve, the need for robust security measures becomes increasingly vital.
In summary, the Salt Typhoon breach serves as a stark reminder of the vulnerabilities that persist within our telecommunications systems. By implementing proactive measures and fostering a culture of cybersecurity vigilance, stakeholders can work together to safeguard sensitive information and maintain public trust in digital services.